London, UK | 020 3997 7979
SentinelOne vs Microsoft Defender for Endpoint
13 April 2022 | ITHQ Tech Team
SentinelOne and Microsoft Defender are both endpoint protection solutions designed to help organizations secure their networks and devices against cyber threats. Both products offer features such as real-time protection, threat detection and response, and malware removal ... but which one is best for you?
One key difference between the two products is that SentinelOne offers an extended detection and response (XDR) capability, which is a more comprehensive approach to threat detection and response that involves collecting and analyzing data from a wider range of sources, such as endpoints, networks, and the cloud. Microsoft Defender, on the other hand, is primarily focused on endpoint protection.
SentinelOne is a third-party security solution, while Microsoft Defender is a built-in security feature
of Windows 10. This means that Microsoft Defender is already installed and configured on all Windows 10 devices, while SentinelOne needs to be installed and configured separately.
In terms of pricing, Microsoft Defender is generally considered to be more affordable than SentinelOne, as it is included with Windows 10 at no additional cost. SentinelOne, on the other hand, is a paid solution and pricing can vary depending on the specific features and number of devices covered.
Overall, both SentinelOne and Microsoft Defender can be effective solutions for protecting against cyber threats, but SentinelOne's XDR capabilities and focus on comprehensive threat detection and response may make it a better fit for organizations with more complex security needs. It is important to carefully evaluate the specific needs and requirements of your organization before deciding which endpoint protection solution is right for you.
Endpoint Protection: Key considerations
- Is it easy to deploy and manage?
- Is it dependent on cloud command and control for detection and response?
- How effective has it been against zero-day attacks?
- Do you have feature parity across Windows, Mac and Linux?
- How does it perform in real world test scenarios?
- What do other customers say about it?
Comparison of Business Benefits and Features
 |
 |
|
| Business Benefits | ||
| Autonomous prevention, detection, and recovery from threats in real-time. | Cloud dependent |
Yes |
| Fast Recovery |
Partial (AIR on E5) |
Yes - Can be automated or 1-click |
| OS freedom (Windows / Mac / Linux feature parity) |
Yes | Yes |
| Fewer alerts with more context |
Incident based |
Yes |
| AI-powered prevention, detection, response, and threat hunting. | Explorer - manual storylines | Yes |
| API integration |
Yes | Yes |
| Scalability | Yes | Yes - Support for containers and serverless workloads, especially Kubernetes dynamic workloads. |
| Higher accuracy across entire attack surface. | Yes - attack surface reduction enhancements. | Yes - Consistent identification of tactics and techniques in the MITRE Phase 2 evaluations. |
| Centralised Visibility | Yes | Yes - full storyline. |
| Automation & Control | Yes | Yes - Automated mitigation options via the Storyline Active Response Capability. |
| Data analytics | Yes | No - SentinelOne does not have its own network security sources to add. |
|
Collection and reporting of; inventory, config and policy management of endpoint devices. |
Yes - e.g. threat intelligence reporting. | Yes |
|
Mobile Threat Defence |
Yes | Yes |
|
Ease of deployment |
No - no on-premise console. |
Yes - Excellent timeliness and quality of customer support. |
| Features | ||
|
AI across user endpoints, containers, cloud workloads, and IoT devices. |
No - dropped support for E-o-L systems. |
Yes - New IoT discovery and protection capabilities in its Ranger product. |
| Static & Behavioural AI |
Heuristics |
Yes |
| Exploit protection | Heuristics | Yes + context |
| Lateral movement | Heuristics | Yes + context |
| Remediation | Automated |
Automated |
| Rollback | No |
Automated |
| Integrated threat feeds | Yes |
Yes |
| Remote shell | No |
Yes |
| Device control | Yes - Device Discovery |
Yes - Device discovery via Ranger. |
| Firewall control | Yes |
Yes |
| Bluetooth control | Yes | Yes |
| Threat hunting |
Yes |
Yes - full storyline |
| Deep visibility | Yes - Sandbox (deep analysis) |
Yes |
| Event Correlation | No |
Yes |
| Execution Restriction | Yes - EDR in block mode. | Yes |
| Vulnerability scanning | Yes - UEFI scanning. | Yes - Priority list of vulnerable applications. |
| Security patching | No | Yes |
| Triage | Yes - decision-making algorithms. | Yes - Investigate in seconds with automated correlations and Storyline. |
| Disk Encryption | No | No - Missing add-on for fully featured DLP. |
Industry and Peer Reviews
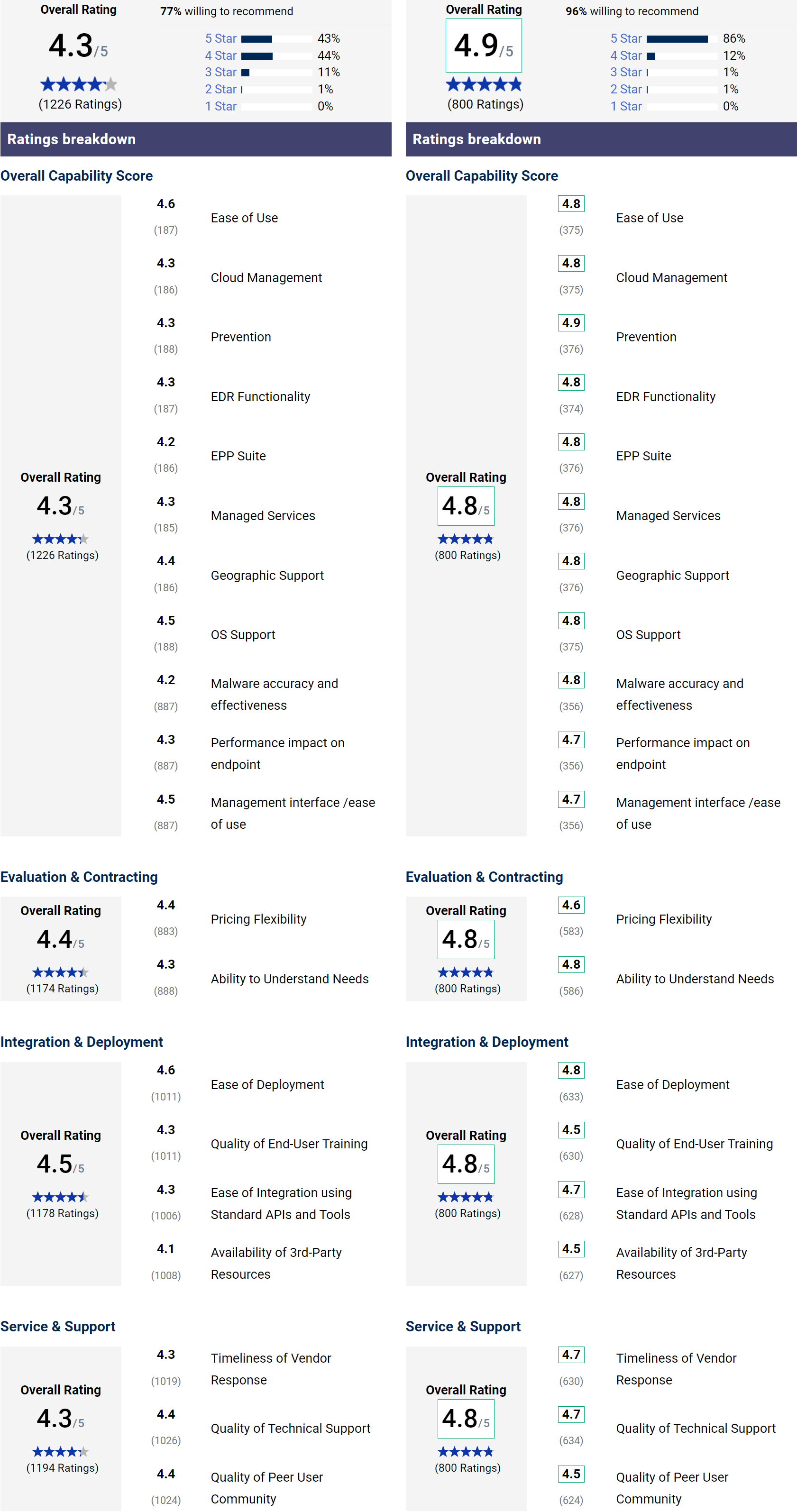
Gartner Peer Insights
|
|
|
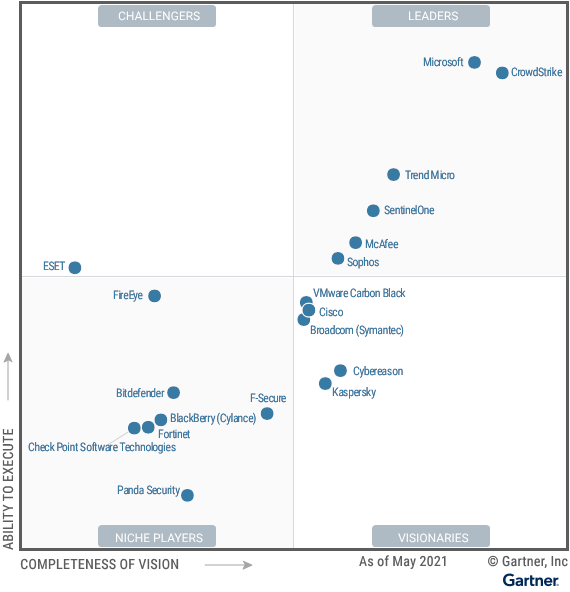
Gartner Magic Quadrant for Endpoint Protection Platforms May 2021
Independent Testing
 |
TESTING BODY |
 |
| Provided coverage across the attack chain stages |
APT29 2020 |
Scored record results:
|
| N/A |
 |
Top ROI score and Recommended rating 2019 |
| NOT CURRENTLY CERTIFIED |  |
99.8% block rate across Windows testing |
|
Top Product for Windows Only 1 false-positive |
 |
100% protection against zero-day malware attacks on Windows |
 |
 |
In top 10 vendors Recognized for the commitment to pushing the boundaries of autonomous technology — delivering innovation at scale and speed, and shaping the endpoint market. |
|
Above average UI launch time Below average memory usage Quickest file copy, move and delete time Longest file compression/ decompression time |
 |
Performs better than several legacy AV products for the following:
|
Pricing
All prices calculated at per endpoint per month, for comparison purposes.
Pricing is 'starting from' and based on list pricing. It can be subject to change, volume discounts etc.
Correct at February 2021
Contact us for accurate pricing based on your specific requirements
|
Minimum purchase - 5 endpoints - only through ITHQ Payment can be billed monthly - only through ITHQ To achieve these prices below, minimum purchase 100 endpoints, billed annually. Quote always required for accurate pricing |
||
| Core | Control | Complete |
| $4.16 | $4.90 | $9.00 |
| Includes full advanced EDR |
All Core features plus device, firewall and bluetooth control |
All Control features plus threat hunting and deep visibility |

Minimum purchase - 100 endpoints
Payment always billed annually
Priced according to Microsoft
$22.00 per user per month
Can't be bought separately – requires Microsoft 365 Business Premium.
This means that to buy security from Microsoft, you have to effectively buy email, the office suite, Azure AD, Windows 10, Teams, OneDrive, Sharepoint, Bitlocker, SCCM and more.







