London, UK | 020 3997 7979
SentinelOne shows record EDR performance in MITRE ATT&CK APT 29 report
02 September 2020 | Andrea Efstathiou
With the lowest missed detections and highest number of high-quality detections, SentinelOne achieved fantastic results in this year’s MITRE ATT&CK APT29 evaluation of endpoint security platforms.
- Why does MITRE ATT&CK matter to the CISO and SOC?
- MITRE evaluation process
- SentinelOne's Record Results Illustrated
Why does MITRE ATT&CK matter?
MITRE is now established as a complex, detailed scoring framework to evaluate a product’s ability to provide actionable information to the SOC. MITRE ATT&CK emulates APT29, the threat group attributed to the Russian government operating since at least 2008, to assess EDR threat detection capabilities.
MITRE aims to promote a common language around cybersecurity and an innovative approach to tool effectiveness evaluation. It describes its framework as “a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target.”
Key words are phases and behavior. When an adversary has a strategic objective – think data exfiltration or establishing long term command and control – they will use multiple, phased tactics.
Each phase consists of behaviors which are simply a set of techniques. Techniques, in turn, have varying sets of procedures. Therefore, the end goal comprises an initial tactic (comprising one or more techniques), followed by another tactic, and so on until the malicious objective is met.
This layering of general tactics down to specific procedures is where we get TTP: Tactic, Technique, Procedure.
In the 2020 testing, out of 21 vendors, SentinelOne:
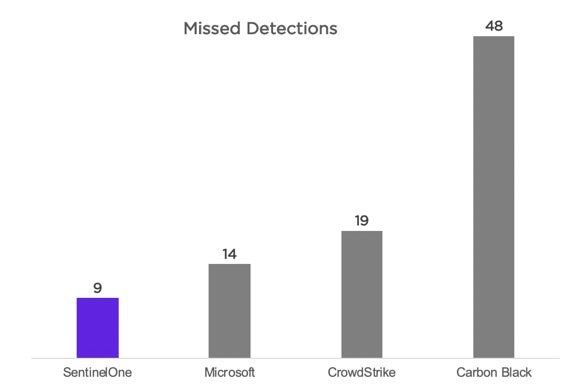
- Missed the lowest number of detections
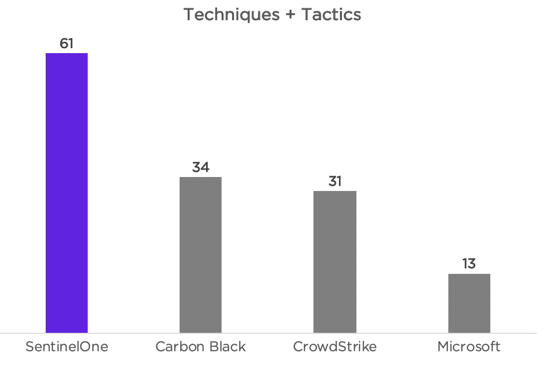
- Achieved the highest number of combined high-quality detections
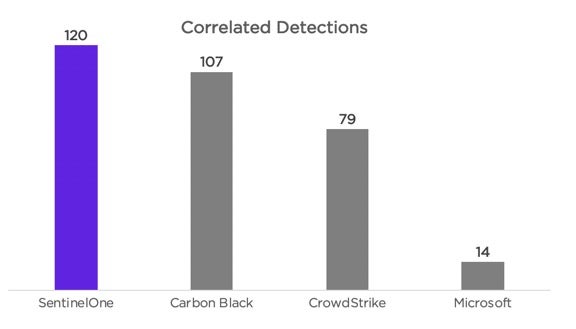
- Achieved the highest number of correlated detections
- Automatically grouped hundreds of data points over the 3-day test into 11 correlated console alerts for highly contextualised results
How MITRE ATT&CK evaluates EDR tools using two scenarios over three days
Six clear steps, with a total of 135 sub-steps, are followed during the execution of two specific attack scenarios.
Scenario One: Starts with the execution of payload delivery via a broad "spray and pray" spearphishing campaign, followed by a rapid "smash and grab" collection and exfiltration of specific file types.
Following initial data theft, the value of the target is realized, and the adversary drops a secondary, stealthier toolkit used to further explore and compromise the target network.
Scenario Two: Focuses on a very targeted, methodical breach. Initially a specially crafted payload is deloyed, designed to scrutinize the target environment before full execution begins. A low and slow takeover of the initial target follows, eventually engulfing the entire domain.
Both scenarios include executing previously established persistence mechanisms after a simulated time lapse to further the scope of the breach.
Each of these stages is completed using selected Tactics, Techniques and Procedures (TTP) mapped in the MITRE ATT&CK framework.
SentinelOne's Record Results
SentinelOne excelled against 20 other vendors. Here's how they did across the main measures of EDR capability.
Lowest Number of Missed Detections
Highest Number of 'Techniques plus Tactics' High Quality Detections
Highest Number of Correlated Detections
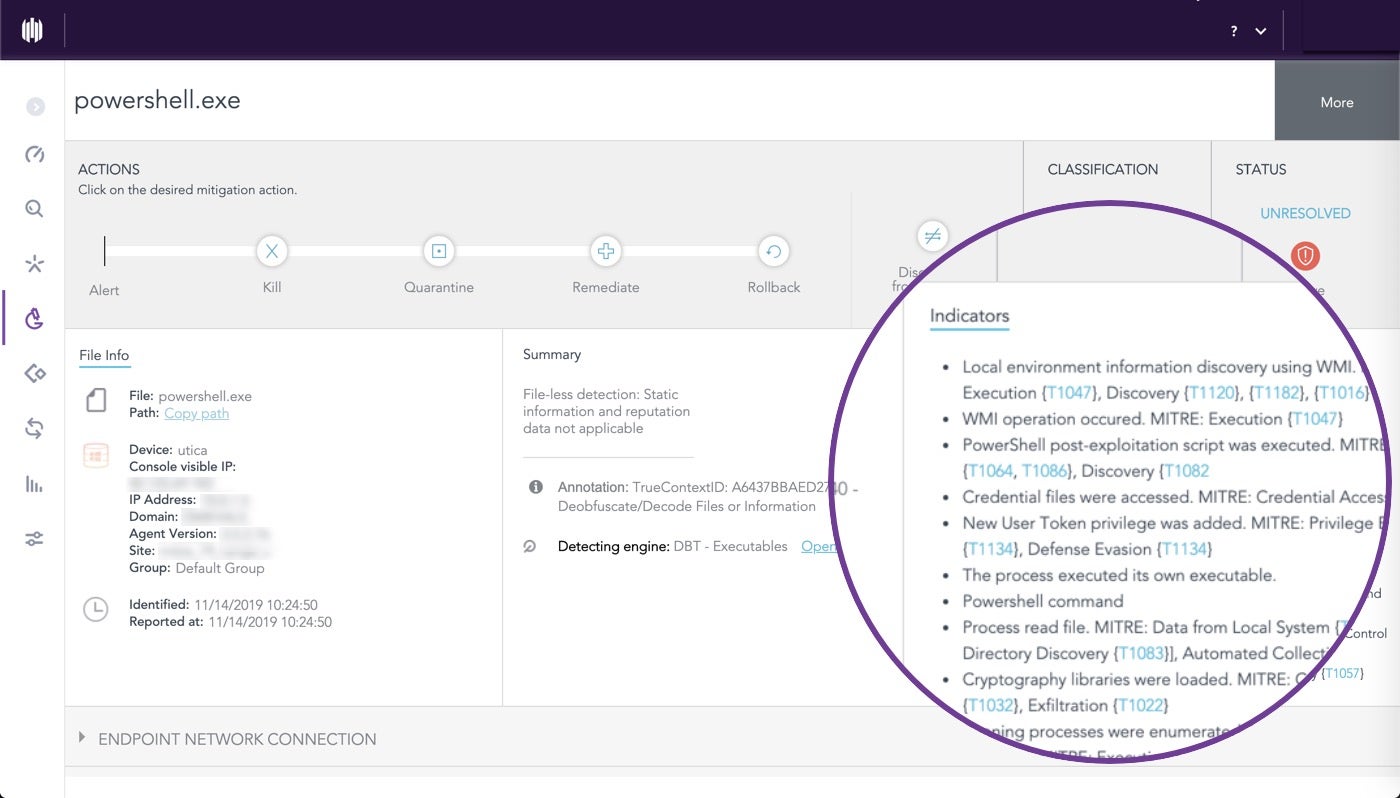
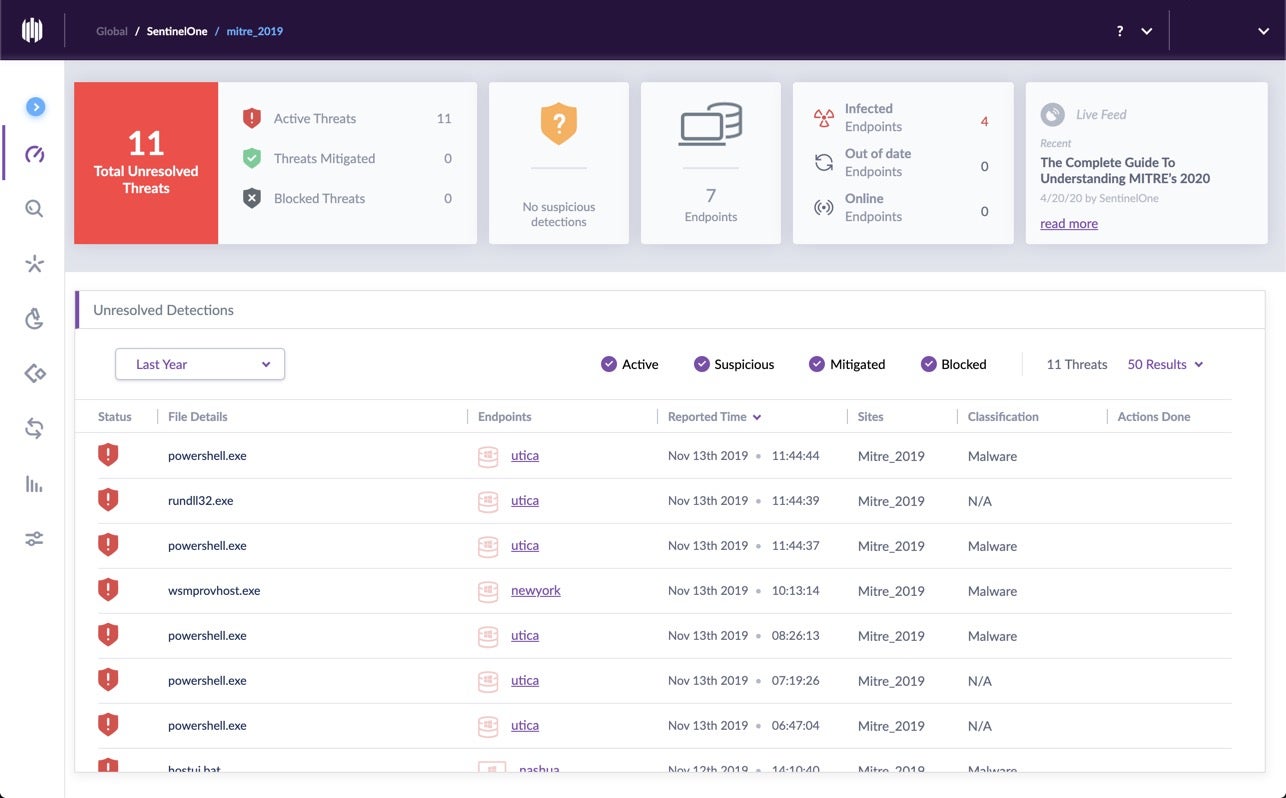
SentinelOne contextualised hundreds of data points into 11 alerts
More data does not mean it's all useful. SOCs need contexualised, prioritised alerts so that analysts can see what's happening immediately in terms of actionable storylines.
Below, you can see how the entire MITRE ATT&CK Round 2 testing battery is captured in the SentinelOne console with just 11 alerts.
Get a demo of SentinelOne and talk to us about the best pricing options. We are able to offer the most flexible packages, from 5 endpoints and monthly billing upwards.



