London, UK | 020 3997 7979
Cyber Resilience
Ransomware? If your business uses data, you’re a target
08 September 2020 | Andrea Efstathiou
If you don’t consider your business an obvious target for ransomware criminals, you need to think again.
Your business data means money for a malicious attacker. If you don't have adequate security, it's only a matter of time until they make you a victim.
Your data doesn't have to be sensitive or your business a particular size. If you use a computer and store all your business-critical information on anything more technological than a ledger, cyber criminals could hold your business to ransom.
It’s not a question of being outsmarted by genius hackers. Or that your businesses operates in a specific sector. The truth is, anyone can be a ransomware criminal now. And anyone can be a target.
Cyber criminals are now often opportunistic amateurs, effectively doing nothing more sophisticated than rattling door latches all over town. If they find one unlocked, in they go.
Encrypting data and making you pay to get it back is their business. They don’t care what your business is.
Cybercrime IS paying because businesses make it too easy for criminals to win
Cybercrime damages are (now famously) predicted by Cybersecurity Ventures to reach $6 trillion by 2021.
This represents the greatest transfer of economic wealth in history. It will make cybercrime more profitable than the global trade of all major illegal drugs combined.
Commercialised ransomware is not about making a point against capitalism or politics, it is only about making money by encrypting data; making us all targets.While IT analysts struggle over forecasting how dramatic the rise in cybercrime will actually be, the cyber security market is expected to only reach $1 trillion in the same timeframe.
It should not be a surprise that criminals are enjoying such a profitable time, when businesses are simply not investing enough in protecting themselves.
Amateur criminals are taking IT pros to the cleaners with RaaS
Hopefully you’re not reading this blog because you’ve Googled Ransomware-as-a-Service (RaaS) following a costly attack. Hopefully, you’re researching how to prevent falling victim to ransomware before anything awful has happened.
I’m afraid, if you still believe you couldn’t possibly be a target, you are probably the best kind of target for these criminals.
Being a cybercriminal no longer requires being a skilled hacker with a political point to make. They just need a computer and a bitcoin account.
Once they’re on the dark web, it’s as simple as selecting a site and signing up, as you would for any number of SaaS business offerings.
Cybercriminals write ransomware code and request a fee. The subscriber gets a neat little malware package including technical tips and an attack launch plan. Any ransom collected is then shared between service provider, coder and attacker.
RaaS examples: Cryptonite and SMAUG
Cryptonite quickly made its mark as a RaaS posterchild.
Ransomware has been around for decades; the hacker-as-a-service model is not new. What set Cryptonite apart was their professional shopfront.
This illegal operation could be mistaken for a legit tech service business. Their site even showcased press mentions, boasted number of infected websites and included a support feature.
Their vision: to enable people 'with just basic computer knowledge' to become a Ryuk ransomware cybercriminal.

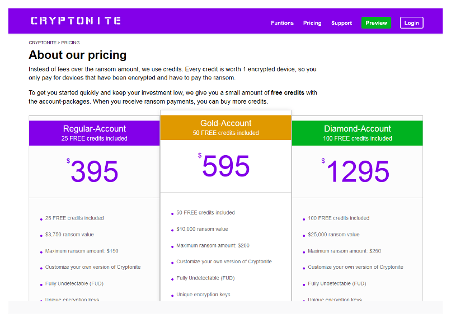
The Cryptonite site is no longer anywhere to be found, but the people behind it could well be behind one of the many other RaaS operations past and present.
SentinelLabs reports that public RaaS offerings were already plentiful a few years ago: SATAN, Nemesis, Petya, RaaSberry, Shark and Data Keeper all featuring as 'service' providers.
The new kid on the block right now is SMAUG, launched in April 2020. This RaaS aims to raise the bar again, with a complex mixture of advanced malware, a SaaS-like user experience and interface, and even a political stance.
The intro page talks about how you 'Become Agent', with 'features' such as customisable campaigns, and automated payments highlighted with snappy icons.
The eye is drawn to UX USPs, such as 'seamless' experience across OS platforms and a smooth payment process for victims.
Politics appears in the Ts & Cs, where users are warned that 'Infecting CIS is forbidden and will result in a ban'.
The CIS referred to stands for 'Commonwealth of Independent States': the group of now independent countries that were once part of the Soviet Union.
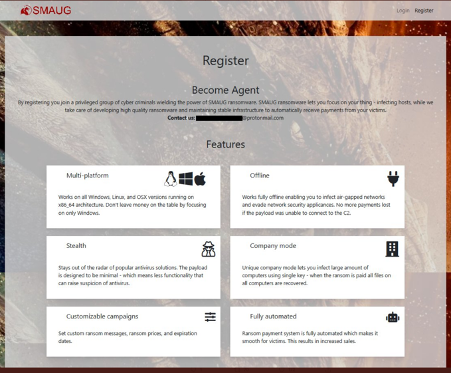
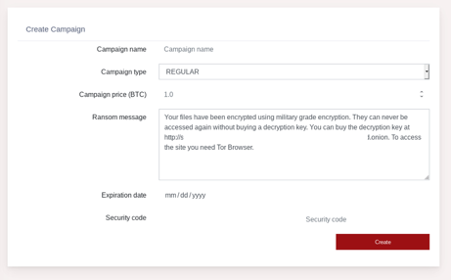
SMAUG might be 'military grade' encryption but it doesn’t require much intelligence to deploy it.
The point is that RaaS can turn someone with minimal coding experience into a criminal capable of holding a business to ransom for millions.
Regardless of the sophistication of the code behind the attack, most RaaS types are still deployed via phishing emails or exploit kits.
Still think a ransomware attacker is a criminal mastermind specifically targeting your business? Or are they simply opportunistic thieves, looking for a way in?
Serious cyber criminals are also looking for unlocked doors
Of course, there are also real-deal cyber criminals out there. Yet they too are largely looking for systems to compromise, rather than specific businesses to target. Weak defences and vulnerabilities are what they seek; they just want access to your data.
Your physical security might include locks, cameras and security personnel. Does your cyber security have the same layers of detail?
The only way to ensure cyber criminals don’t find a way onto your network is to protect your business with layered defence - and to deploy advanced threat detection and response, in case they do.
What is the best ransomware defence?
Traditional anti-virus is not enough.
SMAUG, for one, is designed to sail straight through traditional AV platforms whilst leaving a minimal or even undetectable signature, creating a path for further infections.
Firewalls are not enough – with newly remote workforces now deployed outside the corporate firewall. And if your staff don’t know what a malicious email looks like, they can effectively hold the door open while malware does its worst.
Remote working is driving rapid change in how enterprises protect their data with Service Access Secure Edge (SASE) adoption accelerating beyond all expectations.
This interconnected approach to network security is so new experts have yet to formally agree on its name, with Secure Cloud Access and Policy Enforcement (SCAPE) being another contender.
Gartner coined SASE (pronounced 'sassy') as a term in August 2019, describing it as a way for enterprises to protect their data, wherever it may be located, through a combination of software-defined WAN (SD-WAN), secure web gateways, cloud access security brokers (CASBs) and zero-trust network access.
What is the best easy ransomware defence fix?
If you are concerned about where to begin, you should definitely be looking at next generation endpoint protection that includes ActiveEDR and threat hunting.
Once your endpoints are protected in this way, at least you know ransomware will be stopped before it gets started.
We recommend SentinelOne. Watch it defeat Maze ransomware in 2 minutes.
(We can offer minimum 5 endpoints and monthly payments. SentinelOne also comes with a built in warranty)
Endpoint protection such as this means that if malware does make it onto a machine, it will be instantly detected and quarantined.
The attackers will simply have to rattle someone else’s door.
Ideally, your cyber defence should now include:
- Next Generation Endpoint Protection
- Autonomous cyber security (preferably that comes with some sort of warranty for insurance)
- Next generation firewall
- Threat intelligence and security data analytics
- Zero-trust access
- A business continuity plan that includes rollback
- Staff security training including how to spot malicious activity and emails




